CIS 527
Lab 5.A - Reverse Proxy
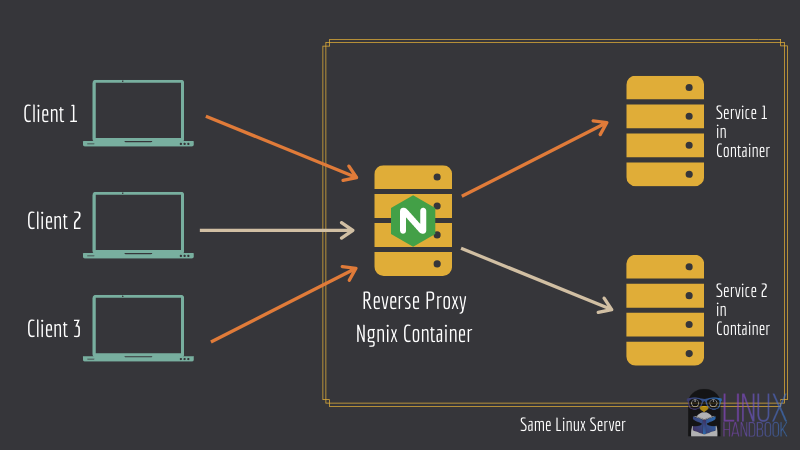
Image Source: Linux Handbook
Option 1 - Nginx
services:
nginx:
image: nginx:alpine
container_name: proxy
ports:
- "8080:80"
volumes:
- /home/cis527/docker/proxy:/etc/nginx/templates:ro
networks:
- default
- internal
whoami1:
image: jwilder/whoami
container_name: whoami1
networks:
- internal
whoami2:
image: jwilder/whoami
container_name: whoami2
networks:
- internal
networks:
internal:
internal: trueOption 1 - Nginx
# /home/cis527/docker/proxy/default.conf.template
server {
listen 80;
server_name one.local;
location / {
proxy_pass http://whoami1:8000;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_buffering off;
proxy_request_buffering off;
proxy_http_version 1.1;
proxy_intercept_errors on;
}
}
server {
listen 80;
server_name two.local;
location / {
proxy_pass http://whoami2:8000;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_buffering off;
proxy_request_buffering off;
proxy_http_version 1.1;
proxy_intercept_errors on;
}
}Option 1 - Nginx
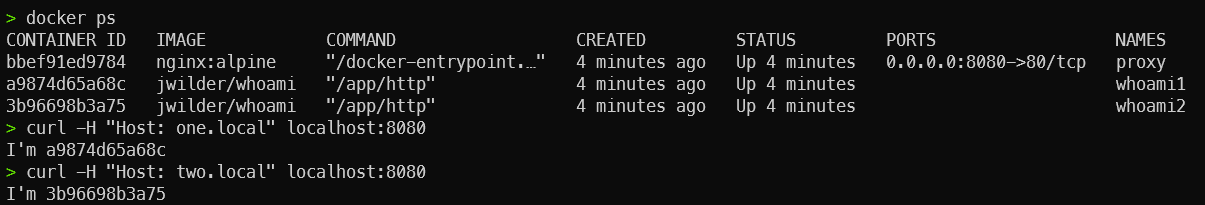
Option 2 - Nginx Proxy
services:
proxy:
image: jwilder/nginx-proxy:latest
container_name: proxy
ports:
- "8080:80"
volumes:
# Security Concern!
- /var/run/docker.sock:/tmp/docker.sock:ro
networks:
- default
- internal
whoami1:
image: jwilder/whoami
container_name: whoami1
networks:
- internal
environment:
- VIRTUAL_HOST=one.local
- VIRTUAL_PORT=8000
whoami2:
image: jwilder/whoami
container_name: whoami2
networks:
- internal
environment:
- VIRTUAL_HOST=two.local
- VIRTUAL_PORT=8000
networks:
internal:
internal: trueOption 2 - Nginx Proxy
Security Concern
- Uses Docker Socket
- Allows Detection of Containers
- root in container = root on host
- Secure using TLS
- Protect via proxy
- Don't expose to internet!
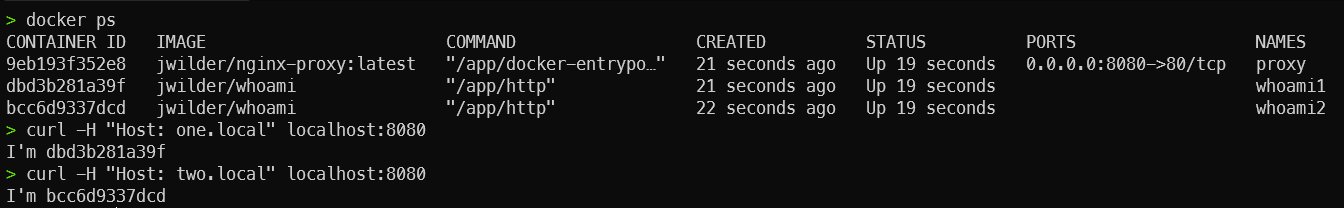
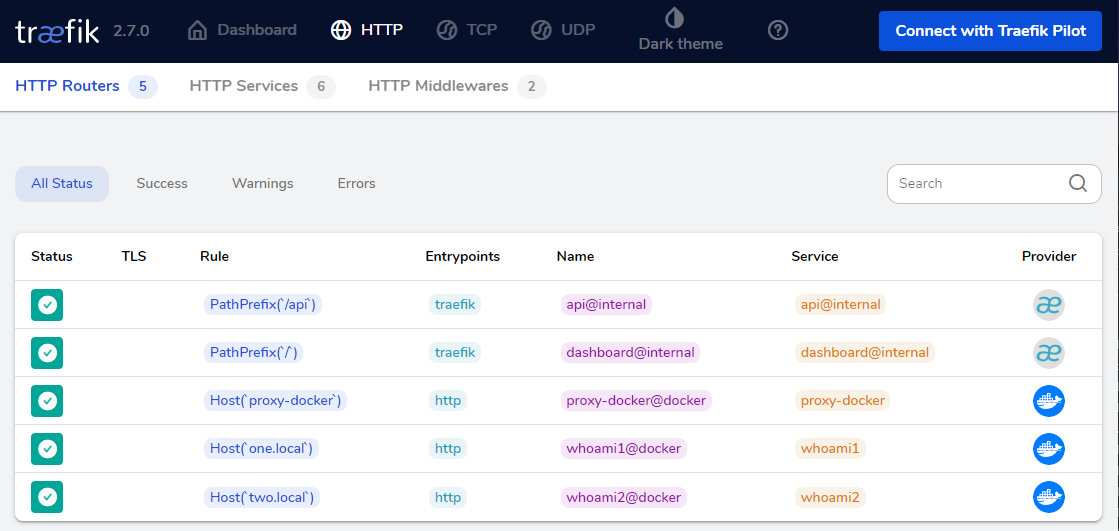
Option 3 - Traefik Proxy

Image Source: Traefik
Option 3 - Traefik Proxy
services:
proxy:
image: traefik:v2.7
container_name: proxy
command: --api.insecure=true --providers.docker
ports:
- "8080:80" # proxy
- "8081:8080" # web dashboard
volumes:
# Security Concern!
- /var/run/docker.sock:/var/run/docker.sock
networks:
- default
- internal
whoami1:
image: jwilder/whoami
container_name: whoami1
networks:
- internal
labels:
- "traefik.http.routers.whoami1.rule=Host(`one.local`)"
- "traefik.http.services.whoami1.loadbalancer.server.port=8000"
whoami2:
image: jwilder/whoami
container_name: whoami2
networks:
- internal
labels:
- "traefik.http.routers.whoami2.rule=Host(`two.local`)"
- "traefik.http.services.whoami2.loadbalancer.server.port=8000"
networks:
internal:
internal: trueOption 3 - Traefik Proxy
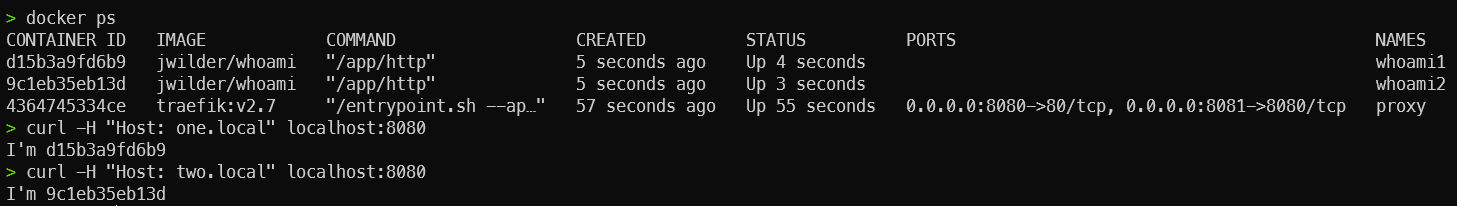
Option 3 - Traefik Proxy
Summary
- Nginx
- Nginx Proxy
- Traefik
- Many Others
Kubernetes handles this for you